Hi folks! Welcome to Day 8 of 100 Days of AWS🎯, where we will cover the complete AWS cloud from beginner to professional. Today, we will expand our horizons in the AWS cloud by Understanding Default VPC and its settings. Stateful and Stateless firewall. types of traffic & firewall. security group vs Network Access control list. and lastly, complete networking architecture. Let’s get started🚀!
Day 7 Overview;
On Day 7 we discussed extensively about what is the role of VPC in AWS, CIDR block range to apply for our VPC, Subnets and type of Subnet, and several Gateway Networking devices for enabling communication between different networks. and methods of connecting the customer’s on-prem resource to the AWS VPC.
Types of VPC;
As of now, everyone knows that VPC isolates computing resources from other computing resources available in the cloud. By default, all AWS accounts will have a default VPC which has a configuration defined by AWS in all regions, for easier deployment of certain resources like EC2. A user can create more than one VPC and modify all configurations associated with VPC as per application need, they are called as custom VPC.

Default VPC & its setting;
In this section, we will look at how our Default VPC which is provided by AWS by default is configured.
AWS will create a default VPC specific to all regions. and have /16 IPv4 CIDR block. 172.31.0.0/16 which has a total IP address of 65,536 addresses.
and have a default subnet for each availability zone with /20 CIDR block containing a total of 4096 IP addresses.
Internet Gateway is attached to the VPC. so by default VPC and all its subnet will have internet access.
A Default Route Table with a route that points all traffic (0.0.0.0/0) to the Internet gateway.
A default security group & Network ACL are attached to the VPC. where the Security group allows outbound access and NACL are open in both Inbound and Outbound directions.

Traffic & its types;
Traffic typically refers to the flow of data or information across a network. traffics can be classified into various ways depending on various factors like the nature of communication, its protocol and the behaviour of the data. but here we will be sticking to the topic and discussing traffic categories in networking for security and management. they are,
Inbound Traffic;
traffic that originates from external sources and comes into the network or system.
eg: user requests to access a web application.
Outbound Traffic;
Traffic that originates from within a network and goes out to an external destination.
eg: response from a server to a user’s request.
Internal Traffic;
Traffic that moves between the devices or services within the same network or infrastructure.
eg: communication between services in the data centre or within VPC
Firewall;
A firewall is a network security service that controls the incoming and outgoing traffic to and from resources. such as Amazon EC2 instances, databases, and other services. based on specified security rules.
It helps protect your AWS resources from unauthorized access allowing only legitimate communication.
Types of Firewalls;
Types of firewalls depending on the way they allow inbound and outbound traffic of a request by using state are,
Stateless Firewall,
Stateful Firewall
Stateless Firewall;
Stateless Firewall must be configured to allow both inbound and outbound traffic.
A stateless firewall treats each packet independently, without keeping track of the connection state. (i.e., whether the packet is part of the ongoing session).
It simply evaluates each packet based on pre-defined rules (like source/destination IP, Port, and Protocol) and applies the rule to either allow or block the traffic.

for example, consider a user is trying to access the webpage running in the web server on port 443. A request is made by the client’s application such as a web browser with a source port as any ephemeral port (1024-65535) and the destination port as 443.
now the server receives the inbound traffic so we have to allow port 443 in firewall Inbound rules. and once the web server processes the request and sends the response back with the source port as a 443 and the destination port as any ephemeral port (1024-65,535) now in order to send the response back successfully to the client we need to grant access to the ephemeral port in the outbound rule. only then the response will reach the client.
Stateful Firewall;
stateful firewall is more advanced and tracks the state of active connection.
It is aware of the context and the state of each connection passing through it. making decisions based not just on rules but also on whether the traffic is part of an ongoing session.
by default when you launch a new instance in AWS. a default security group is assigned to it.
the default security group has no inbound rules. ( meaning no inbound traffic is allowed by default)
the default security group allows all outbound traffic.

Stateful firewalls are intelligent enough to understand which requests and responses are part of the same connection. means that if a request is permitted, the response is also permitted in the stateful firewall.
for example, consider the same previous example where a user sends the request from a client-side application such as a web browser where the source port is any ephemeral (1024-65535) and the destination port is 443.
now the firewall will keep track of the connection state so it will automatically allow the response of the request without any rules.
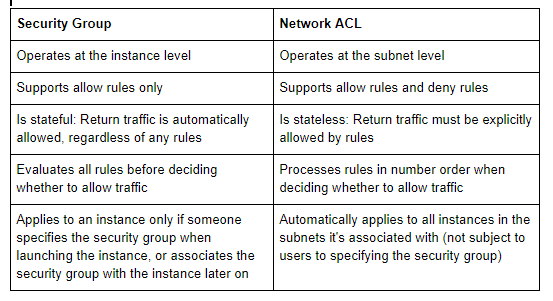
Security Group;

Network Access Control List (NACL);
NACLs filter traffic entering and leaving a subnet. it is a subnet-level firewall.
The default behaviour of NACL in AWS is designed to allow all inbound and outbound traffic. unless you specifically configure certain rules to deny certain types of traffic.
NACLs do not filter traffic originating within the subnet.
They are stateless firewalls so rules must be set for both the Inbound and Outbound traffic.
The default NACL automatically includes two rules for both inbound and outbound traffic,
Rule 100: Allow all traffic (inbound and outbound).
Rule 32767: The default "deny all" rule, but it’s at the end and is not used unless you create rules before it.

Security Group vs NACL;

Complete Networking Architecture;

Day 8 Wrap Up;
In conclusion, Day 8 of our 100 Days of AWS journey has provided a comprehensive understanding of networking basics within the AWS cloud. We explored the intricacies of Virtual Private Clouds (VPCs), including the differences between default and custom VPCs, and delved into the configurations that make up a default VPC. We also examined the types of network traffic and the role of firewalls in securing AWS resources, distinguishing between stateless and stateful firewalls. Furthermore, we compared Security Groups and Network Access Control Lists (NACLs), highlighting their unique features and applications. This foundational knowledge is crucial for effectively managing and securing AWS environments. As we move forward to Day 9, we will continue to build on this knowledge, further enhancing our AWS expertise.
Summary & Key Points;

Every region has a Default VPC with default subnets, Security Groups, and NACLs. the CIDR block for default is 172.31.0.0/16.
The Default VPC and its subnets have outbound access to the Internet by default. One default subnet in each Availability Zone.
Stateless firewalls require traffic to be explicitly permitted inbound & outbound Stateful firewalls are intelligent firewalls that track requests and allow response.
Network ACLs filter traffic entering & leaving a subnet
Security Groups act as firewalls for individual resources such as EC2, NICs, and other network objects.
Up next on Day 9;
Types of Storage.
AWS Storage Basics.
